SQUID PROXY INSTALLATION
Install squid proxy using available package manager. Since I had to install squid on a RHEL server, I used yum.
sudo yum -y install squid
Start the squid proxy service and check the status to see if its running.
sudo systemctl start squid
sudo systemctl status squid
The squid proxy configuration file can be found in /etc/squid/squid.conf. The config file will consist of rules (ACLs), IP networks from where browsing (http_access) should be allowed and other configuration options. The following were the default contents of the config file.
#
# Recommended minimum configuration:
#
# Example rule allowing access from your local networks.
# Adapt to list your (internal) IP networks from where browsing
# should be allowed
acl localnet src 10.0.0.0/8 # RFC1918 possible internal network
acl localnet src 172.16.0.0/12 # RFC1918 possible internal network
acl localnet src 192.168.0.0/16 # RFC1918 possible internal network
acl localnet src fc00::/7 # RFC 4193 local private network range acl localnet src fe80::/10 # RFC 4291 link-local (directly plugged) machines
acl SSL_ports port 443
acl Safe_ports port 80 # http
acl Safe_ports port 21 # ftp
acl Safe_ports port 443 # https
acl Safe_ports port 70 # gopher
acl Safe_ports port 210 # wais
acl Safe_ports port 1025-65535 # unregistered ports
acl Safe_ports port 280 # http-mgmt
acl Safe_ports port 488 # gss-http
acl Safe_ports port 591 # filemaker
acl Safe_ports port 777 # multiling http
acl CONNECT method CONNECT
#
# Recommended minimum Access Permission configuration:
#
Squid Proxy Installation 1
# Deny requests to certain unsafe ports
http_access deny !Safe_ports
# Deny CONNECT to other than secure SSL ports
http_access deny CONNECT !SSL_ports
# Only allow cachemgr access from localhost
http_access allow localhost manager
http_access deny manager
# We strongly recommend the following be uncommented to protect innocent # web applications running on the proxy server who think the only
# one who can access services on “localhost” is a local user
#http_access deny to_localhost
#
# INSERT YOUR OWN RULE(S) HERE TO ALLOW ACCESS FROM YOUR CLIENTS
#
# Example rule allowing access from your local networks.
# Adapt localnet in the ACL section to list your (internal) IP networks # from where browsing should be allowed
http_access allow localnet
http_access allow localhost
# And finally deny all other access to this proxy
http_access deny all
# Squid normally listens to port 3128
http_port 3128
# Uncomment and adjust the following to add a disk cache directory.
#cache_dir ufs /var/spool/squid 100 16 256
# Leave coredumps in the first cache dir
coredump_dir /var/spool/squid
#
# Add any of your own refresh_pattern entries above these.
#
refresh_pattern ^ftp: 1440 20% 10080
refresh_pattern ^gopher: 1440 0% 1440
refresh_pattern -i (/cgi-bin/
\?) 0 0% 0
refresh_pattern . 0 20% 4320
Note: If you’re using apt package manager to install squid for Debian based Linux system (like Ubuntu), then the default squid.conf file may be very long. Instead of working with that conf file, you can rename it by running mv squid.conf squid.conf.bkp and copy the contents shown above into a new squid.conf file.
In the conf file, you can specify the sources from which squid proxy should accept connections as shown below. For more configuration details, check Reference 1 and 2
Squid Proxy Installation 2
# For a single host access
acl broadbits-host src 10.0.0.22/32
# For access to a network
acl broadbits-net src 10.10.10.0/24
Allow http_access to the host/network specified in above acl.
http_access allow broadbits-host
http_access allow broadbits-net
After making the configuration changes, test if the proxy is working by running the following curl command.
curl -x http://<squid-proxy-server-IP>:3128 -I http://google.com
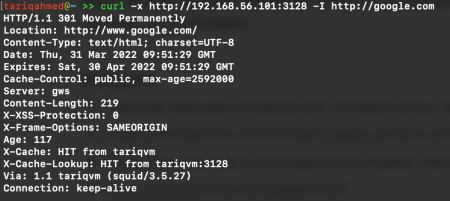
Note: If a firewall is enabled, add a firewall rule to accept connections on port 3128. In my case, the firewalld service was running on the RHEL server. Add a firewall rule using the iptables command.
sudo iptables -I INPUT -p tcp -m tcp –dport 3128 -j ACCEPT
Squid Proxy Installation 3
Configure Proxy Authentication
Install httpd-tools on the proxy server (Centos). If its Debian, install apache2-utils.
# Centos
sudo yum install httpd-tools
# Debian
sudo apt-get install apache2-utils
Create a password file and make squid as the file owner.
sudo touch /etc/squid/passwd && sudo chown squid /etc/squid/passwd
Note: In my case, there was no squid user. So instead, I gave file ownership to root user.
Now, create a custom username and password for authentication. Add a username to the password file using htpasswd utility. It will prompt for a custom password. This username and password will be used for all connections through this proxy. In my case, username is tariq-squid and password is abc .
Note: I have used a weak password for testing purposes. Always use a strong password in production!
sudo htpasswd /etc/squid/passwd tariq-squid
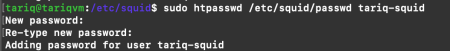
Add the following configurations to the beginning of the /etc/squid/squid.conf file.
auth_param basic program /usr/lib/squid/basic_ncsa_auth /etc/squid/passwd auth_param basic children 5
auth_param basic realm Squid Basic Authentication
auth_param basic credentialsttl 2 hours
acl auth_users proxy_auth REQUIRED
http_access allow auth_users
Restart the squid service.
Squid Proxy Installation 4
sudo systemctl restart squid
Now, test the proxy connection from another system using curl. You will get the “authentication required message” as shown below.
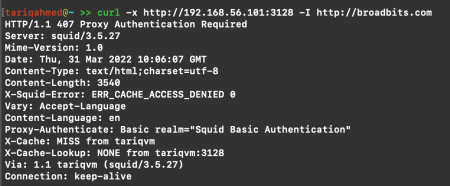
Test the connectivity with the proxy username and password. In my case, the user is tariq-squid and password is abc .
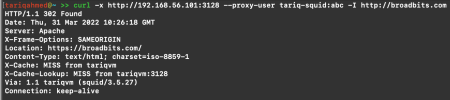
You have successfully configured squid proxy with authentication! References
- https://devopscube.com/setup-and-configure-proxy-server/
- https://www.tecmint.com/configure-squid-server-in-linux/
- https://docs.rackspace.com/support/how-to/allow-web-traffic-in-iptables/
- https://stackoverflow.com/a/50544307
